David Emm, principal security researcher in Kaspersky’s Global Research & Analysis Team (GReAT), recently spoke to students about the evolution of ransomware into the fortified ecosystem it is; and what this means for the cybersecurity community. Here are the highlights:
From indiscriminate attacks costing hundreds of pounds to targeted attacks costing millions
The modern era of ransomware has become increasingly targeted. In the early days, ransomware was distributed indiscriminately – aimed at anyone and everyone it could reach. Attackers would encrypt data using unsophisticated methods and hope for a pay out of maybe £300. Their sometimes rudimentary encryption methods meant that cybersecurity experts could not only detect the threat but could often also decrypt the data – a near impossibility today.
Ransomware developers have since realised that there is much more money to be made by targeting specific organisations. Instead of a few hundred pounds, they can get hundreds of thousands of pounds, and even millions in some cases. The number of ransomware samples and blocked attacks is on a downward trend but this is only because attackers are focusing on more strategic and impactful attacks rather than on quantity.
The 2017 WannaCry ransomware epidemic underlined the impact that a ransomware attack can have on organisations. WannaCry affected 230,000 computers around the world in total, but showed the catastrophic impact on specific organisations. The ransomware affected thousands of NHS hospitals and surgeries across the UK and reportedly caused ambulances to be rerouted. The NHS is estimated to have lost £92 million as a result and the global cost of related attacks was estimated at $4 billion.
In some instances, this ransomware isn’t even necessarily designed to get money – just to sabotage IT systems. This was the case with NotPetya in 2017, which had a significant impact on a number of organisations. For example, hipping company, Maersk lost between $200 and $300 million as a result of this ransomware attack.
Networked versus hierarchical structure
When most people imagine these ransomware gangs, they picture an Ocean’s Eleven-style set up, run by a great criminal mastermind – and for law enforcement agencies, this would be a far easier adversary to overcome. Instead, ransomware has evolved from individual hierarchical structures into a fully-fledged modular ecosystem– a whack-a-mole system of replaceable players.
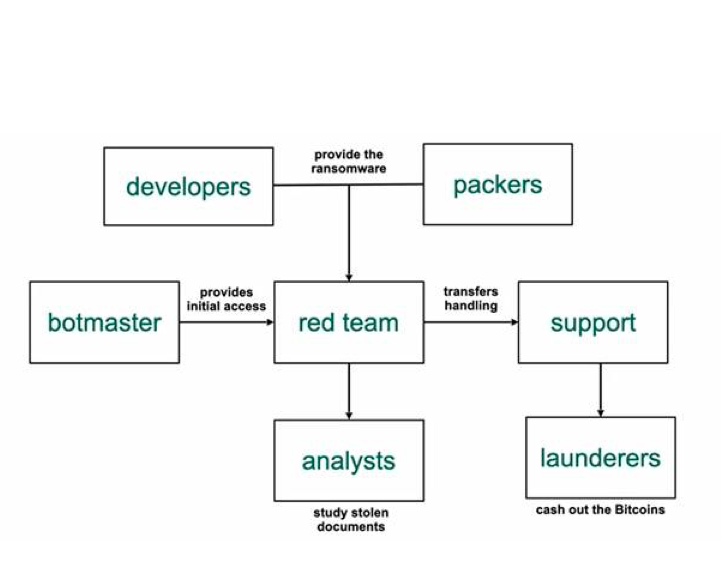
Pictured; diagram of the players within this whack-a-mole ransomware ecosystem.
•The botmaster: controls the botnet, a robot network of compromised computers under the control of an individual(s) who looks to monetise their point of contact on all compromised computers. This includes through Infrastructure-as-a-Service, Crimeware-as-a-Service or Malware-as-a-Service
•Developers: develop the ransomware program and sell their creation to others in the ecosystem
•Packers: pack purchased ransomware to make it as fully undetected as possible when it is deployed in the target system
•The red team: does the attacking, extending the initial compromise into the wider organisation
•Analysts: determine which information is most sensitive and this is used as leverage for ransom demands
•Support team: liaises with relevant people in the organisation to persuade them to pay the ransom, explaining that decrypted data will be lost or published if payment is not received
•Laundering: seized money is laundered to make it difficult to track. The rise of digitised and electronic payments and banking have made this easier
How do cybersecurity experts advise as best practices in this climate?
With today’s ransomware, cybersecurity experts are rarely able to find a mechanism for decrypting data. This makes backups, a proactive defence plan and crisis management plans imperative.
•Backups – Backups do not completely mitigate the impact of an attack, as ransomware still needs to be removed and IT teams need to clean up and restore the backup, but they do allow data loss to be minimised and enable companies to save the extortionate money demanded as a ransom. However, not all backups are created equal – if you can access it, so can the attackers, and it is going to be vulnerable to encryption. So backups must be stored offline. IT teams also need to periodically test that backups can be restored in the event of a crisis.
•Crisis management – IT teams need to make sure their organisation has a plan for secure communications in the event of a ransomware attack. If regular communications are used to interact between teams, attackers will be privy to such communications and can use them as leverage. An alternative plan needs to be developed and practised.
•Proactive defence – Organisations need to implement solutions that allow them to analyse network behaviour for suspicious activities and block attacks before they can cause damage. They also need to implement effective education strategies. This will make employees less prone to falling victim to phishing and other social engineering methods used by attackers to trick staff into running malicious code.
Ramsomware gangs are making millions of pounds and, even scarier is the prospect of what they can do with those earnings in terms of reinvesting into their own R&D. Our latest research found that nearly 75 per cent of UK organisations paid the attackers in order to get their data back. However it is good practice to avoid paying ransoms because this is the oxygen that keeps these groups alive.
Nevertheless, vulnerable organisations are put in extremely difficult circumstances – particularly those operating critical infrastructure facilities – because of the impact on business continuity and subsequent reputational damage. It is worth noting that Kaspersky was a founding member of NoMoreRansom, now a broad consortium of industry and police bodies providing free decryptors for victims of ransomware attacks.
As ransomware groups become increasingly formidable, it is the duty of those in the cybersecurity sector to ensure that they are at the forefront of industry trends, developing new and innovative solutions to protect our increasingly interconnected world.
That said, over two-thirds (68pc) of firms are not able to handle a ransomware attack even with an internal IT team despite the fact that almost the same number (65pc) consider these attacks a high possibility, according to a recent Kaspersky survey, “How business executives perceive ransomware threat?”. Insufficient technical skills amongst employees are one of the biggest challenges for businesses when dealing with complicated cyberthreats.
How do we encourage the next generation of cybersecurity professionals?
Many people think that they need a computer science degree in order to enter the profession. However, there is a variety of different roles within the industry and a broad range of skills that are needed: not just mathematicians, cryptographers and programmers, but people with writing skills, communications skills and more. Technical skills are important, but equally so is curiosity. For anyone aspiring to a career in cybersecurity, I would recommend Jessica Barker’s “Confident Cyber Security: How to Get Started in Cyber Security and Futureproof Your Career”.
The way we handle ransomware has completely changed in the last 15 years or so. The next generation of cybersecurity professionals has a daunting task ahead, staying one-step, and preferably a few ahead of ransomware gangs and other types of attacker. Just as they are evolving, so too is our industry. Every year our abilities to defend against cyber-attacks becomes stronger and more innovative.
That’s why Kaspersky has expanded its online expert training portfolio, designing and developing a new self-guided Windows Incident Response training course for in-house cybersecurity teams and InfoSec professionals looking to upgrade their skills. The course teaches extensive theory around the subject along with real applied skills through end-to-end ransomware case investigation. It consists of 40 video lessons and 100 hours of virtual lab time for hands-on learning. Participants can finish training in an estimated 15 hours, but they have up to six months to complete the course.
By the end of training, participants learn know how to identify and respond to cyber incidents, differentiate advanced persistent threats (APTs) from other threats, master evidence acquisition, the phases of incident detection, log file analysis, network analysis, how to create indicators of compromise (IoCs), introductory memory forensics, various attack techniques and the anatomy of a targeted attack through the cyber kill chain.
Today’s cybersecurity solutions go way beyond the old-fashioned pattern detecting approach characterised as ‘anti-virus’ – including the use of generic detection, heuristics, behavioural analysis, emulation and sandboxing techniques. Our experts are continually developing new systems to stay ahead of the latest threats.