Complex is a term that is often used to describe the technological make up of modern web applications. They are like onions, made up of intricate layers where, if not designed or secured appropriately, can foster many critical vulnerabilities. Therefore, it’s necessary for organisations to know the key attack vectors and system entry points used by the modern hacker to better understand their overall attack surface, writes Stephane Konarkowski, Senior Security Consultant at the cyber security and vulnerability assessment firm Outpost24.
Only by locating these flaws, organisations can begin to implement the right security controls in the right places to protecting their web applications, given that these are often the gateways to business shopfront. In fact, successful web application attacks pose a serious threat, as they account for almost half of all data breaches (43%) in 2019 and are the single greatest cause of data breaches according to the Verizon DBIR 2020 report.
Web applications are typically where sensitive customer and financial data is collected and stored, making it one of the first places a hacker will target. Also, with the majority of businesses focused on business continuity during the global pandemic, security to some may have not been a priority – a concerning fact given hackers are continually evolving their tactics to break into web applications to extract sensitive data. Some may think that good security hygiene and WAF alone will prevent such a disastrous scenario but unfortunately even some of the biggest brands suffered from simple application exploits. Examples include an incident where there were a lack of authentication controls (First American Financial), publicly available servers (Facebook) and the infamous Fortnite breach when a vulnerability allowed a cross-site scripting (XSS) attack where thousands of users were tricked into clicking a link planted by an attacker, contributing to millions, even billions, instances of customer data being leaked.
Hackers are masters of reconnaissance when selecting a target, duly gathering information on the potential victim to locate weak spots on the systems before initiating the attack. Therefore, businesses that do not address the issues within their online infrastructure are underestimating the will of the modern hacker. The slightest error spotted could give a hacker the pathway to your crown jewels and get a piece of your pie without you noticing.
So, how does one go about mapping the entire attack surface of the web application and identify the deadly attack vectors that can get you hacked?
This can be broken down into three stages starting with application discovery. Organisations should have an itinerary of what critical web apps they own and where they are being exposed. But here in lies a problem as the number of apps and associated vulnerabilities could easily be in the thousands, especially in larger organisations where shadow IT is prevalent, so it’s vital to locate the publicly exposed web apps at a regular cadence to eliminate blind spots.
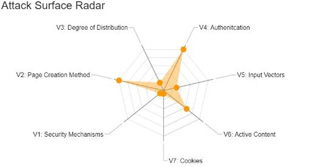
The second stage is to assess the risk level of web applications identified against the 7 most common attack vectors that hackers use to exploit software vulnerabilities:
•Vector 1 – Security mechanisms – This determines the how web traffic between users and the application is secured
•Vector 2 – Page creation method – Depending on what coding language and web design program could lead to more security problems
•Vector 3 – Degree of distribution – More pages means there’s more potential to encounter issues which means all pages must be monitored
•Vector 4 – Authentication – Verification of the identity of a legitimate user accessing the web application. All access privileges must be reviewed and should be restricted to only those that need it
•Vector 5 – Input vectors – The more input fields, the greater likelihood the attack surface will increase which can lead to cross site scripting attacks
•Vector 6 – Active contents – When applications run scripts it initiates active contents and depending on the way those scripts have been implemented, the attack surface could increase if a website has been developed using several active content technologies
•Vector 7 – Cookies – These are required for real time application security to help with monitoring session activity. They also help keep hackers away from unauthorised areas.
Once the web applications have been checked against the above threats, correlates the results against business criticality and update frequency to determine the overall risk posture. By truly understanding the total addressable attack surface, including areas of weakness and strength, you are then able to implement the right security controls at the right place.
Security teams must act on this information to ensure effective and continuous application testing is included in the overall security programme. Risk scores displayed on the attack surface radar gives a visual representation of where security efforts should be directed – by focusing on the most critical of threats. By applying this level of security insights to web applications, you will not only improve customer experience and business growth but, most importantly, it will remove your business from the crosshairs of hackers.