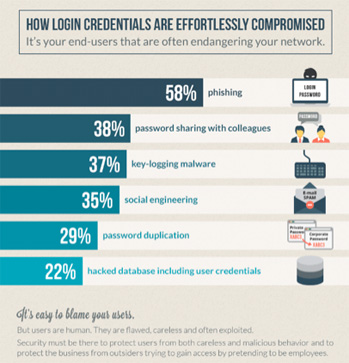
Compromised credentials constitute one of the most dangerous threats to an organisation. The reason for that is quite simple: those attacks are extremely difficult to detect because the cybercriminal owns valid credentials. Of course they have been stolen, but they are still valid especially in the eyes of your security tools which will not detect any suspicious activity. So, when the hacker logs in, the security solutions you have in place consider that this person is who they say they are. Here is IS Decisions’ research into the access security priorities of 500 IT security managers in the US and UK; from François Amigorena, the founder and CEO of IS Decisions, a provider of infrastructure and security management software solutions for Microsoft Windows and Active Directory.
This is where multi-factor authentication (MFA) comes in. It constitutes one of the most robust control to prevent unauthorized access. Without MFA, all of your other security measures can be bypassed.
This risk is now well known, and still a large number of businesses don’t take it seriously enough. Our research from a couple of years ago showed that only 38 per cent used MFA. What’s more worrying is that according to more recent research, things haven’t really changed today.
Multi-factor Authentication is being misconceived.
1.MFA is for organisations of all sizes
Many organisations think “my company is too small, I don’t need MFA”. Well, they’re wrong. The data they’re trying to protect is as sensitive as any large enterprise. Any company, regardless of size, should be using MFA to protect their user accounts. It doesn’t have to be complex, costly of frustrating.
2.MFA should be used to protect all users
Many organizations also think “I don’t have any privileged users so I don’t need MFA”. Wrong again. MFA should be used to protect all users in your organization. The reason is that even though they don’t have access to critical data, they still have access to a large amount of information that, if used inappropriately, could end up harming your company. Take a nurse for example, what happens if she decides to sell a celebrity patient’s data to a journalist?
The second reason you should protect all of your users is that attackers usually don’t start with a privileged account. Most of the time they start with an “easy” account and once they get access to the network, they move laterally until they can find valuable data.
3.MFA is not perfect but it’s close
In information security, perfect doesn’t exist. But to be honest, MFA is close. Recent attacks showed that MFA could be bypassed. The FBI issued a warning about those events. Two main authenticator vulnerabilities were found: ‘Channel Jacking’, involving taking over the communication channel that is used for the authenticator and ‘Real-Time Phishing’, using a machine-in-the-middle that intercepts and replays authentication messages.
These attacks necessitate a lot of money and efforts according to specialists. Usually, cybercriminals who come across MFA will switch to an easier target rather than try to bypass it. A number of vulnerabilities can be avoided by choosing MFA authenticators that do not use SMS authentication. (The National Institute of Standards and Technology (NIST) discourages SMS and voice in its latest Digital Identity Guidelines).
Despite the recent events, the FBI still maintains that MFA is highly effective.
4.MFA doesn’t have to be disruptive
Employee’s productivity is very important to any business and it’s always a challenge when implementing a new solution. If you want the adoption to be easy and fast, you need as little disruption as possible. With MFA, you need flexibility and customization. To do so, MFA can be used in conjunction with contextual controls to improve identity assurance. This means using environmental information to further verify all users’ identity without disruption.