Unmanned Aerial Vehicles (UAVs), or drones as they are more frequently described are everywhere and growing in number. Ten million drones in circulation today are forecast to grow to 50 million by 2025. Once the sole province of military or government agencies, drones are now widely available to mainstream customers with minimal outlay, and while practical to businesses and enjoyable for enthusiasts and hobbyists alike, they present a significant and evolving threat, writes Steve Hearn.
Over the last few years UAV threats have largely evolved into four key areas; weaponised or attack drones, smuggling, snooping or eavesdropping and airspace near miss incidents.
Risks
Misuse of drones in the context of airspace collision risks are well known and documented and need no further explanation. The number of near miss and inappropriate flights near commercial airspace are increasing, both in number and worryingly in the altitude at which they are being flown. Reports have recently detailed near miss incidents at many thousands of feet as drones become ever more able to make long high endurance flights. The Civil Aviation Authority (CAA) legislates regularly to prevent these risks and continue to instigate controls to restrict drone flights in controlled airspace.
The use of weaponised drones is now open to anyone who can turn an off the shelf commercially available drone into an improvised explosive device. Many UAVs can carry significant payloads and an IED can readily be made following instructions openly available on both the conventional and dark web. Historically, on an average week over 25 IED drone attacks were initiated by ISIS fighters in Syria, and with some of these trained activists now returning to the UK this approach may soon be deployed on the mainland. It’s easy to imagine a scenario where a drone is launched from a remote site and sent on a fully automated flight for up to 25 minutes to deliver its payload. By the time it’s been delivered the pilot can be many miles away from the launch site. It is perhaps a case of not if, but when.
We have all heard of incidents whereby drones are used to smuggle drugs, phones and other contraband into prisons and many will have seen CCTV footage of such deliveries taking place, often direct to specific windows, showing great skill by the pilot in control. Recently a major organised crime gang was disrupted by prison intelligence offers and the police after they had used drones to smuggle drugs, weapons and mobile phones worth an estimated £1.2 million into prisons across the country, leading to prison sentences for the gang totalling over 32 years. Fast emerging as a significant risk however is the use of drones in delivering prohibited items and drugs to restricted open air venues such as festivals and open-air concerts. Sporting events, university campus sites and even hospitals have all reported incidents of inappropriate use of drones and accordingly a strong approach to combat such use must be developed.
Probably the most eye-opening and fastest developing area is the use of drones for eavesdropping, spying and industrial espionage. Of course, they have been used for many years to obtain paparazzi style footage of celebrities and VIP events, and will no doubt continue to be used in such a manner in the world of free press. It’s the wider use of drones to infiltrate networks, snoop and spoof WIFI access points and to undertake surveillance activity for corporate espionage that presents a real and on the most part an uncontrolled risk. Obtaining company sensitive data and financially or commercially beneficial information are obvious uses, however drones have also been also used to spy on football training sessions to gain tactical insights to better place decisions on the gambling markets. If you can think of it, drones can probably now do it! What was historically done by humans at great risk can now be undertaken by a UAV and confident pilot with little cost and little skill.
What to do
Ask many security professionals what can be done to counter drone threats and more likely the conversation will turn to counter measures and the need to “take the drone out”, either by signal jamming, electronic fencing or net guns and impact munitions to knock the drone out in flight. Whilst all options are feasible and indeed available, the fact remains that most if not all of these options are illegal in the United Kingdom and for the most part can only be deployed by government agencies under strict authorisations. So, what can be done to counter the unmanned aerial vehicle threat.
You don’t know, what you don’t know
Drone Impact, like most counter drone specialists would advocate a three-step approach to mitigating airspace threats. Detection, Protection & Reaction
1. Detection
Whilst significant resources are spent protecting sites through the deployment of intrusion detection, target hardening programs, surveillance and guard force deployment, the emerging risk from aerial threats remains largely uncontrolled. There is a need for a third dimension to the protection package that counters threats to the uncontrolled airspace above.
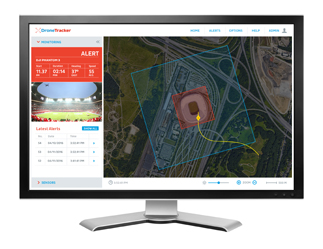
Many businesses are unaware as to the nature or extent of airspace threats, and implementing a scalable countermeasures program based on what might be happening is inappropriate at best. Far better to fully understand the threat landscape and plan your risk strategy accordingly. An airspace incursion audit should be the first undertaking in your risk mitigation plan. Long range RF scanners assisted by intelligent software and reporting tools can, over a suitable period of say 30 days, give a full and detailed view of just what risks you face. Of course, this may prove that you face no threat, however in our experience many businesses are surprised by just how many flights and incursions have been detected.
2. Risk Protection and Airspace Awareness
This is in effect an enhanced version of phase one but with more emphasis placed on understanding the UAV’s in your airspace and capturing forensic data, along with giving a high-profile view of your action plan. The complexity and cost associated with this phase will largely depend on the risk you face, your risk appetite and governance standards however, all plans will generally follow the same route.
For businesses with little or no UAV risk, you may seek to simply continue with random airspace audits and to publicise your actions to act as a strong deterrent. Those with a greater risk variant may wish to plan for more frequent airspace surveillance and auditing via a managed service, or look to installing their own permanent system, leveraging the available RF detection capabilities with state of the art video analytics to give the best possible detection and warning of airspace threats at distances that give sufficient time to respond. Software integration is readily available that can drive many security countermeasures and smart building integrations giving you the option to automatically trigger defensive actions as part of your UAV Reaction Plan.
Wider integration across geographical areas can also offer the opportunity of providing a total detection approach. The City of London has for many years been at the forefront of ground breaking integrated security solutions to provide the “Ring of Steel” by which the entire square mile is controlled and monitored from a central control room, and entry points provide total control of movements into and out of the city. Distributed sensors and IP cameras strategically placed around the city skyline could easily provide an airspace protection zone complimenting the physical street level approach. Similar wide area approaches could be deployed across wide area estates such as military bases, universities, hospitals or large-scale data centres.
For high risk open air events, sporting venues or during VIP visits, services such as Drone Impacts Drone Sentry are available to provide temporary detection and reaction capabilities. Mobile RF scanning equipment paired with CCTV and analytics software can be deployed to give a wide area protection bubble over the site in order to give early indications of airspace threats. Response plans can then be developed and implemented by trained employees or on-site reaction teams. For more high risk venues and events the outputs from the detection system can be fed to police or management command centres giving an overall awareness of the airspace management, and if required allow senior officers to deploy countermeasures as appropriate and proportionate to the threat.
3. Reaction
Reacting to a drone threat depends on many factors, your own risk approach, vulnerability and threat level to name but a few. In most cases your action plan will be a mixture of active and passive protocols. Passive actions, by their very nature, can almost always be driven by software integration with security architecture that allows semi or fully automated responses and reaction to threats. Simple lockdown, network isolation or shutdown, visibility interruption or cloaking can all be automatically triggered. Systems can send immediate warnings of drone incursions via email or SMS messaging or via onscreen control room notifications to ensure the earliest possible notification. For active measures its favourable to have physical intervention plans that ensure a guard force or employee response plan to get “eyes on” the UAV to verify the threat extent. Options to then trace the drone pilot location can be deployed either via enhanced RF and video triangulation, or by static observation should the pilot be operating in line of sight of the drone.
Emergency service liaison should also form a strand of your plan ensuring that not only can a response to an incursion incident be proportionately planned for, but also to ensure they are aware of the plans and actions you intend to take, and to also ensure full visibility of any forensic evidence that can be provided by your detection system. Many drones can be traced via MAC address and serial numbers and in many cases this data can be captured from a drone whilst being tracked in flight. Finally, as stated earlier, more aggressive interventions to disrupt the UAV in flight are available that can be deployed manually via your guard force, or automatically via software interface. Strict adherence to local and national restrictions associated with such countermeasures must be maintained however.
Conclusion
The threat from UAVs are a newly emerging and ever-changing issue. The methods deployed and the people deploying them are ever growing and evolving, and the pool of trained fighters returning from ISIS campaigns provide a potential pool of dedicated activists able and willing to deploy ever more technically advanced attacks. Provided we take reasonable and proportionate steps to deploy airspace monitoring technology, can contextualise the threat and plan accordingly for an incursion, we can more than mitigate this evolving threat quickly and efficiently. The paradigm shift for traditional security threat planning is to ensure we take in the uncontrolled airspace above our facilities that fall outside of Air Traffic Control scope and to ensure we no longer “Don’t know what we don’t know”.
About the author: Steve Hearn is the founder of Drone Impact, a specialist security practice providing airspace detection and protection services.